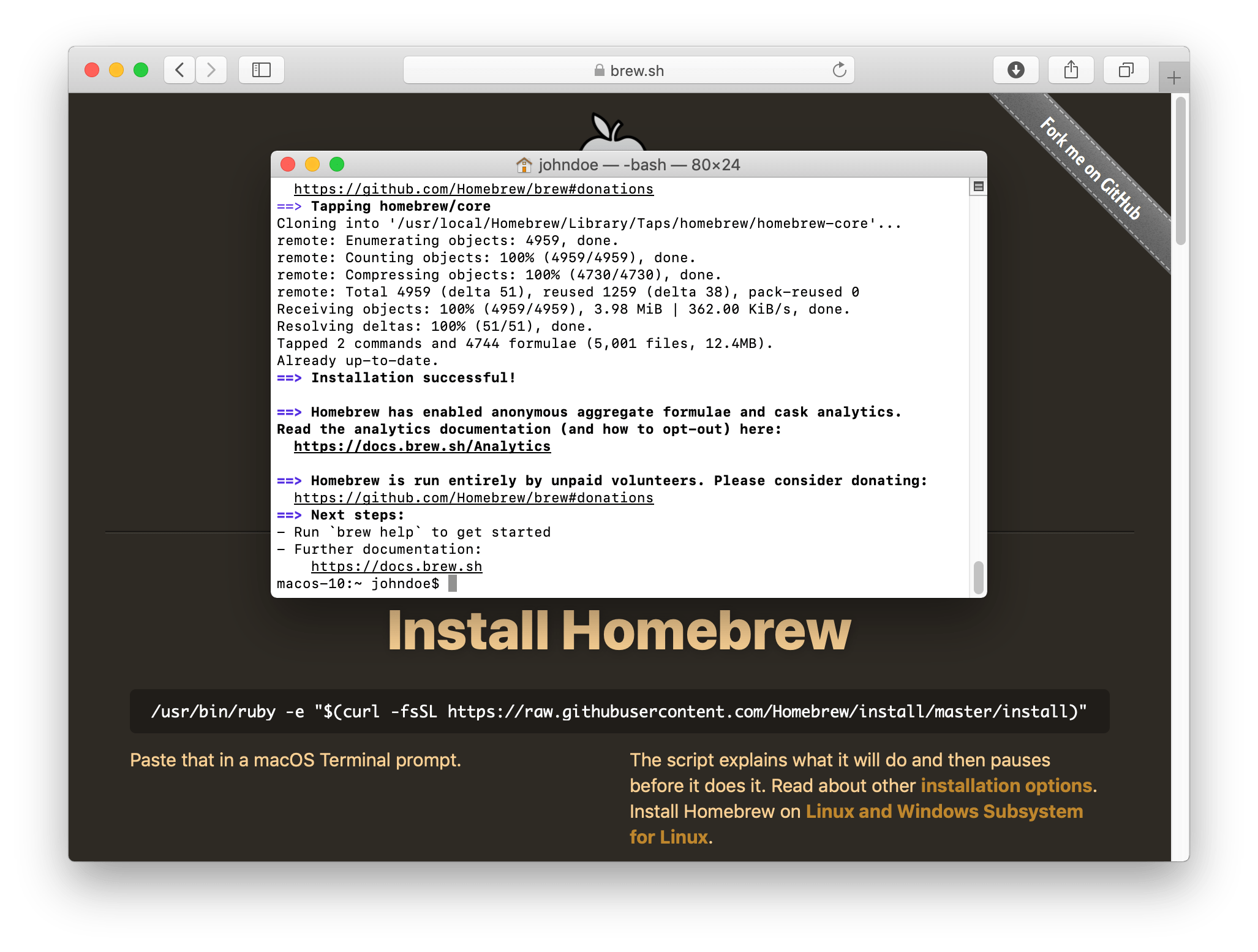
Openvpn Macos Download
On This Page | Release DownloadsTo be notified of new releases, use Tunnelblick's built-in update mechanism or subscribe to the Tunnelblick Announce Mailing List. Beta versions are suitable for many users. See Stable vs. Beta for details. As a Free Software project supported by donations, Tunnelblick puts its users first. There are no ads, no affiliate marketers, no tracking — we don't even keep logs of your IP address or other information. We just supply open technology for fast, easy, private, and secure control of VPNs.
Verifying DownloadsYou should verify all downloads. Even though https:, the .dmg format, and the application's macOS digital signature provide some protection, they can be circumvented. Verifying Hashes Comparing the SHA256, SHA1, and MD5 hashes of your downloaded file with the official published ones will provide additional assurance that the download is legitimate and has not been modified. You can compare the hashes with programs included with macOS without the need to install additional software. To compute the hashes of a file you've downloaded, type the following into /Applications/Utilities/Terminal: shasum -a 256path-to-the-file Then compare the computed hashes with the values shown near the link for the downloaded file. (Don't type 'path-to-the-file' — type the path to the file, that is, the sequence of folders that contain the file plus the file name (e.g. /Users/janedoe/Desktop/Tunnelblick_3.7.2a_build_4851.dmg). An easy way to get it into Terminal is to drag/drop the file anywhere in the Terminal window. The pointer will turn into a green and white plus sign ('+') to indicate the path will be dropped. So you would type 'shasum -a 256 ' — with a space after the '256' — and then drag/drop the disk image file anywhere in the Terminal window.) For additional assurance that the hashes displayed on this site have not been compromised, the hashes are also available in the description of each 'Release' on Tunnelblick's GitHub site, which is hosted and administered separately from this site. Verifying GnuPG Signatures Recent Tunnelblick disk images are also signed with GnuPG version 2. To prepare for verifying signatures, you should download and install GnuPG 2.2.3 or higher, and then add the Tunnelblick Security GnuPG public key (key ID 6BB9367E, fingerprint 76DF 975A 1C56 4277 4FB0 9868 FF5F D80E 6BB9 367E) to your trusted GnuPG keyring by typing the following into /Applications/Utilities/Terminal: gpg --import TunnelblickSecurityPublicKey.asc. To verify the signature of a file, download the corresponding signature file and then type the following into /Applications/Utilities/Terminal: gpg --verify path-to-the-signature-filepath-to-the-disk-image-file The result should be similar to the following: gpg: Signature made Sat Dec 16 19:17:03 2017 EST User ContributionsThese downloads have been contributed by users and usually help deal with special circumstances. They are not endorsed or checked by the Tunnelblick project, and you use them at your own risk. To contribute a download, send it to the developers or post it on the Tunnelblick Discussion Group. Before using these scripts, please read Tunnelblick and VPNs: Privacy and Security. (Actually, everyone using a VPN should read that!) Note: these scripts are executed as root.Instructions for using scripts.
Download IntegrityIn June 2015 there was much discussion (and outrage) about SourceForge providing downloads that contain unwanted or malicious software; SourceForge has changed their policies to help avoid this. Tunnelblick binaries were hosted on SourceForge from the fall of 2013, when Google Code stopped hosting new binaries, until 2015-07-17, when they were moved from SourceForge to GitHub. Tunnelblick protects against unwanted software insertions by publishing the SHA1 and MD5 hashes for each of our downloads. You should verify the hashes of all Tunnelblick downloads by following the instructions above. Additional safeguards automatically protect updates performed by Tunnelblick's built-in update mechanism:
Downloading and Installing on macOS Mojave or HigherWhen Tunnelblick is installed after being downloaded normally, macOS Mojave sends information to Apple (it 'phones home') [1]. It is assumed, but has not been verified, that macOS Catalina also does this. This behavior is considered by some to be a violation of privacy. If you want to avoid having macOS Mojave 'phone home' when you install Tunnelblick, you can do the following to download Tunnelblick to your Desktop:
This will download the file to your Desktop without the flag that indicates the file was downloaded from the Internet. When that flag is present, macOS Mojave 'phones home' when the downloaded file is double-clicked; when the flag is not present, macOS Mojave doesn't. You will be disabling security checks which macOS would normally do on a downloaded program, including checks that the program is correctly notarized and has been found to not contain malware. [1] This isn't something peculiar to Tunnelblick – Mojave does this for any program or document downloaded from the Internet using most browsers and some other programs. [2] Tunnelblick downloads are redirected from the tunnelblick.net website to GitHub, which then redirects them further. Typically two or more tiny downloads (a few hundred bytes each) provide information about the redirection, and the final larger download is the desired file. |
Important
Netgate is offering COVID-19 aid for pfSense software users, learn more.
There are three client options for Mac OS X.:
The OpenVPN command line client. Most users prefer a graphical client, so thisoption will not be covered.
Tunnelblick, a free option available for download at the Tunnelblick Website.
The commercial Viscosity client. At the time of this writing, it costs $14USD for a single seat. If OpenVPN is used frequently, Viscosity is a muchnicer client and well worth the cost.

Viscosity for macOS and Windows. Download Viscosity now to trial it for 30-days with no purchase necessary and no limitations. Purchase Viscosity to remove the 30-day trial limitation and help support its development. Viscosity is a one-time purchase, with no subscriptions or recurring fees. We are moving to MSI installers in OpenVPN 2.5, but OpenVPN 2.4.x will remain NSIS-only. Compared to OpenVPN 2.3 this is a major update with a large number of new features, improvements and fixes. Some of the major features are AEAD (GCM) cipher and Elliptic Curve DH key exchange support, improved IPv4/IPv6 dual stack support and more seamless. Download OpenVPN for Mac - Provides quick access to a fully-featured SSL VPN solution which can accommodate a wide range of configurations, and can be managed via a web nterface.
Both Tunnelblick and Viscosity are easily installed, with no configurationoptions during installation.
Configuring Viscosity¶
When using the Viscosity client, it can be configured manually or the OpenVPNClient Export package may be used to import the configuration. Viscosityprovides a GUI configuration tool that can be used to generate the underlyingOpenVPN client configuration. The CA and certificates can be imported manually,and all of the parameters can be set by hand. This section cover importing aViscosity bundle from the export package.
Download a copy of the Viscosity bundle for the client from the OpenVPNClient Export package
Locate the saved file, which will end in
.visc.zipindicating that it is acompressed archiveCopy this exported bundle to a folder on the Mac
Double click this file and it will expand to
Viscosity.viscDouble click
Viscosity.viscand Viscosity will open and import theconnection as shown in Figure Viscosity Import
Delete the
Viscosity.viscdirectory and the.ziparchiveViscosity will be running after import, and may be found in the menu bar
Click the lock icon added to the menu bar at the top of the screen
Click Preferences to check that the configuration was imported as shown inFigure Viscosity Preferences
Viscosity Preferences¶
Check the Connections area to see if the connection imported successfullyas shown in Figure Viscosity View Connections.
Openvpn Mac Os Download 10 13
Close the Preferences screen
Click the lock in the menu bar
Click the name of the VPN connection to connect as shown in FigureViscosity Connect. After a few seconds, the lock in the menu barwill turn green to show it connected successfully.
Mac Os Download Iso
Viscosity Connect¶
Click on it and then click Details as shown in FigureViscosity Menu to see connection information
On the first screen (Figure Viscosity Details), the connectionstatus, connected time, the IP assigned to the client, and the IP of the serverare all displayed. A bandwidth graph is displayed at the bottom of the screen,showing the throughput in and out of the OpenVPN interface.
Viscosity Details¶
Clicking the up/down arrow button in the middle of the details screen displaysadditional network traffic statistics. This shows the traffic sent within thetunnel (TUN/TAP In and Out), as well as the total TCP or UDP traffic sentincluding the overhead of the tunnel and encryption. For connections usingprimarily small packets the overhead is considerable with all VPN solutions. Thestats shown in Figure Viscosity Details: Traffic Statistics are from only afew pings traversing the connection. The traffic sent in bringing up theconnection is also counted here, so the initial overhead is higher than what itwill be after being connected for some time. Also, the typical VPN traffic willhave larger packet sizes than 64 byte pings, making the total overhead anddifference between these two numbers considerably less.
Clicking on the third icon in the middle of the Details screen shows theOpenVPN log file (Figure Viscosity Details: Logs). If there is any troubleconnecting, review the logs here to help determine the problem. See alsoTroubleshooting OpenVPN.
Viscosity Details: Logs¶
